Have you ever accidentally deleted a user account or an OU in Active Directory and wished you could restore it?
I recently had a client call me after they installed updates and
rebooted their server. They noticed after the reboot that there was a
message that said
“Active Directory is rebuilding indices. Please wait”.
Their Active Directory database had become corrupted from the updates. So what do you do? How can you restore AD?
Let’s talk about how to backup AD in Windows Server 2008 and how to restore it. Today I’ll show you:
- what you need to do to get your Server 2008 ready for backup
- how to backup Active Directory on Server 2008
- how to perform an Authoritative Restore of Active Directory
- how to perform Active Directory Snapshots
Prerequisites: Getting Server 2008 Ready for Backup
Before you can backup Server 2008 you need to install the backup features from the Server Manager.
1. To install the backup features click Start → Server Manager.

2. Next click Features → Add Features

3. Scroll to the bottom and select both the Windows Server Backup and the Command Line Tools

4. Click Next, then click Install
Backing up Server 2008 Active Directory
Now that we have the backup features installed we need to backup
Active Directory. You could do a complete server backup, but what if you
need to do an authoritative restore of Active Directory?
As you’ll notice in Server 2008, there isn’t an option to backup the System State data through the normal backup utility.

So what do we do? We need to go “command line” to backup Active Directory.
1. Open up your command prompt by clicking
Start and type “
cmd” and hit enter.
2. In your command prompt type “
wbadmin start systemstatebackup -backuptarget:e:” and press enter.
Note: You can use a different backup target of your choosing
3. Type “
y” and press enter to start the backup process.

When the backup is finished running you should get a message that the
backup completed successfully. If it did not complete properly you will
need to troubleshoot.

Now you have a system state backup of your 2008 Server!
Authoritative Restore of Active Directory
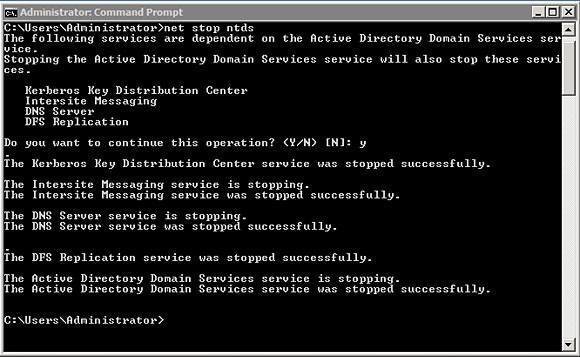
So now what if you accidentally delete an OU, group, or a user
account and it’s already replicated to your other servers? We will need
to perform an authoritative restore of the Active Directory object you
accidentally deleted.
1. To do this you will need to boot into DSRM (Directory Services Restore Mode) by restarting your server and pressing
F8 during the restart.
2.Choose
Directory Services Restore Mode from the Advanced Boot menu.
 3.
3. Login to your server with your DSRM password you created during Active Directory installation.
4. Once you’re logged into your server and in DSRM safe mode, open a command prompt by clicking
Start, type “
cmd“, and press enter.
5. To make sure you restore the correct backup it’s a good idea to use the “
wbadmin get versions” command and write down the version you need to use.
 6.
6. Now we need to perform a non-authoritative restore of Active Directory by typing “
wbadmin start systemstaterecovery -version:04/14/2009-02:39“.
Note: The version of backup will vary depending on your situation. Type “
y” and press enter to start the non authoritative restore.
7. Go grab some coffee and take a break while the restore completes.
 8.
8. You can mark the sysvol as authoritative by adding the
–authsysvol switch to the end of the wbadmin command.
 9.
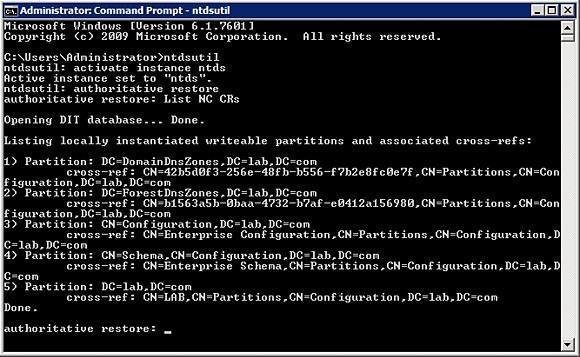
9. But if you want to restore a specific Active Directory object then you can use the ever familiar
ntdsutil.
For this example we are going to restore a user account with a distinguished name of
CN=Test User,CN=Users,DC=home,DC=local. So the commands would be:
ntdsutil
activate instance ntds
authoritative restore
restore object “cn=Test User,cn=Users,dc=home,dc=local”
Note: The quotes are required
 10.
10. Reboot your server into normal mode and you’re
finished. The object will be marked as authoritative and replicate to
the rest of your domain.
Using Active Directory Snapshots
There is a really cool new feature in Windows Server 2008 called
Active Directory Snapshots. Volume Shadow Copy Service now allows us to
take a snapshot of Active Directory as a type of backup. They are very
quick to create and serve as another line of defense for your backup
strategy.
With your server booted into normal mode open a command prompt by clicking
Start, type “
cmd“, and press enter.
We are going to use the ntdsutil again for creating the Active Directory snapshots. The commands are:
ntdsutil
snapshot
activate instance ntds
create
quit
quit

So now that you have a snapshot of AD, how do you access the data?
First we need to mount the snapshot using ntdsutil. The commands are:
ntdsutl
snapshot
list all
mount 1 — (Note: You should mount the correct snapshot you need; for this example there is only 1.)
quit
quit

Your snapshot is mounted, but how do you access the data? We need to
use the dsamain command to accomplish this. Then we need to select an
LDAP port to use. The command is as follows:
dsamain –dbpath c:\$SNAP_200905141444_VOLUMEC$\WINDOWS\NTDS\ntds.dit –ldapport 10001
The result should look like this:

Now we need to go to
Start,
Administrative Tools, then
Active Directory Users and
Computers.
Right click
Active Directory Users and Computers and select
Change Domain Controller.

In the area that says
< Type a Directory Server name [:port] here > enter the name of your server and the LDAP port you used when running the dsamain command.
For my example it would be:
WIN-V22UWGW0LU8.HOME.LOCAL:10001

Now you can browse the snapshot of Active Directory without affecting anything else negatively.
Your AD Backup Strategy
It’s always good to have a solid backup plan for your Active
Directory. You can use a combination of backup strategies or just one of
these methods for backing up your Active Directory.
Make sure you tailor your Active Directory backup strategy to meet
your company’s needs and make it easy to recover if disaster does
strike.
Trainsignal.com