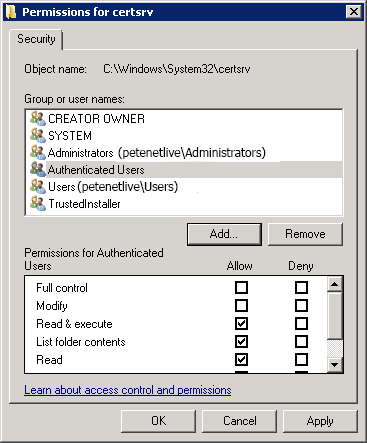
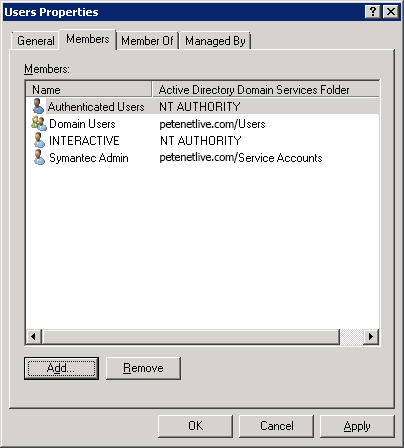
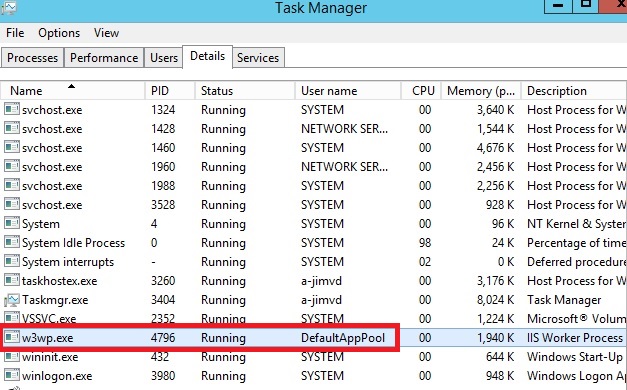
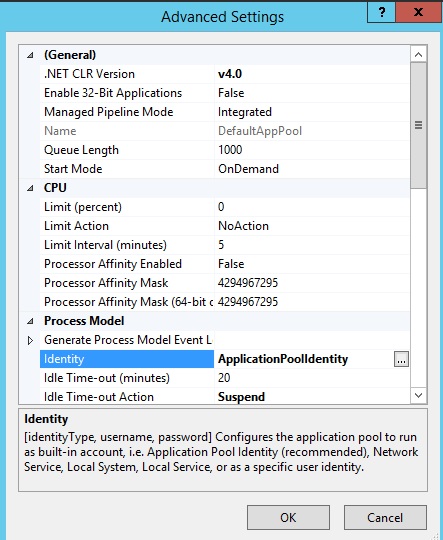
- Hệ thống Quản lý Tài liệu lưu trữ là hệ thống được sử dụng để quản lý, lưu trữ, bảo toàn và phân phối các tài liệu của tổ chức.
- Hệ thống Quản lý Tài liệu lưu trữ nhắm đến mục tiêu làm việc quản lý thông tin trong doanh nghiệp trở nên dễ dàng hơn thông qua việc đơn giản hóa lưu trữ, bảo mật và sử dụng. Nhờ đó, một tổ chức sẽ được nhiều lợi ích như: hiệu suất gia tăng, khả năng kiểm soát tốt hơn và giảm thiểu chi phí.
- Hệ thống Quản lý Tài liệu lưu trữ nhằm tin học hóa và thống nhất các hình thức lưu trữ, trao đổi, tìm kiếm, chia sẻ thông tin hồ sơ trong tổ chức.
- Xây dựng hệ thống các kho Hồ sơ điện tử, khắc phục một cách cơ bản tình trạng mất mát, thất lạc hồ sơ.
- Quản lý toàn bộ hồ sơ của phòng ban, của tổ chức
II. Chức năng dùng chung:
1. Tra cứu hồ sơ:
Người sử dụng có thể tra cứu hồ sơ theo những danh sách lựa chọn:
2. Tìm kiếm nâng cao:
Tại giao diện trang chủ cũng như tại những danh sách tra cứu hồ sơ đều cho phép chọn chức năng tìm kiếm hồ sơ nâng cao.
3. Tìm kiếm toàn văn hồ sơ:
Hệ thống hỗ trợ người sử dụng tìm kiếm toàn văn thông tin của hồ sơ, tìm kiếm theo nội dung file gắn kèm là file có đuôi dạng txt, doc, docx, chuẩn pdf, xls, xlsx…. Tại trang chủ hoặc các trang danh sách đều có ô tìm kiếm toàn văn hồ sơ.
III. Quản lý hồ sơ:
1. Tạo mới hồ sơ (tạo, sửa, xóa):
Đính kèm các văn bản liên quan (nếu có)
Thêm những người có quyền xem hồ sơ.
Khi người sử dụng thêm file đính kèm, xóa file hoặc chia sẻ hồ sơ cho người khác xem, hệ thống sẽ lưu lại lịch sử thay đổi của hồ sơ.
IV. Thùng rác
Những hồ sơ đã xóa sẽ không xóa hoàn toàn khỏi hệ thống mà sẽ được đưa
vào thùng rác, chỉ người có quyền quản trị hệ thống mới thấy được chức năng
thùng rác. Tại chức năng thùng rác người quản trị hệ thống có thể khôi phục lại
hồ sơ đã xóa hoặc xóa hoàn toàn hồ sơ khỏi hệ thống.
Mọi chi tiết xin liên hệ
Hỗ trợ kinh doanh:- Nguyễn Quang Tuấn - 04.62737300, 0912.068.823 (nqtuan@vsd.com.vn)
- Phùng Quốc Hoàn - 04.62737311 (pqhoan@vsd.com.vn)