Support details
This document pertains to HP Notebook PCs with the HP Unified Extensible Firmware Interface (UEFI) beginning in late-2008.
On startup, you may see a blank screen. If the diagnostic utilities detect a specific problem with hardware components, the fan turns on, but the screen remains blank. To help identify the cause of the problem, various LED lights on the keyboard blink a series of codes.
The diagnostic utilities use the LEDs near the Num Lock or Caps Lock keys to blink a series of error codes. At the end of the series the blinking stops. The pattern of blinks will occur any time you attempt to start the computer until the error is resolved.
Battery power LED blinks
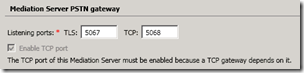
The Battery power LED indicates the condition of the power supply. When starting the computer, or when the computer is in operation, use the chart to identify the power condition.
| Battery Power LED | Component Tested | Error Condition |
|---|---|---|
| Battery power LED off, and Caps Lock/Num Lock off | Battery or AC Adapter | AC adapter not connected or failure Battery low charge or failure |
| Battery power LED blinking | Battery | Insufficient charge on the battery |
 | When new computer is used for first time, the white LED light for the AC power connector blinks. | Battery is still in "Shipping Mode", the light continues to blink even when AC power is connected. To resolve, turn off notebook, connect AC power and allow battery to charge for at least 30 minutes, then start computer. |
LEDs near Caps Lock and Number Lock keys blink when starting notebook
The LED lights near the Caps Lock and Num Lock keys will blink if an error is detected during the start up process. The LEDs will blink a number of times in a sequence and then stop. The number of blinks in the sequence indicates what component caused an error when it was being tested during start up.
If the LEDs stop blinking and the computer does not start, you can press the power button again to repeat the tests. Count the number of blinks, and use the chart to identify the error condition.
Knowing the number of blinks is helpful when you contact an HP support agent for technical help.
| Caps Lock/Num Lock LED | Component Tested | Error Condition |
|---|---|---|
| LEDs blink 1 time | CPU | CPU not functional |
| LEDs blink 2 times | BIOS | BIOS corruption failure |
| LEDs blink 3 times | Memory | Module error not functional |
| LEDs blink 4 times | Graphics | Graphics controller not functional |
| LEDs blink 5 times | System board | General system board failure |
| LEDs blink 6 times | BIOS | BIOS authentication failure |
Error code explanations
The sections below provide some common explanations for each error code listed in the table above.
When the computer is on battery power only and the AC adapter is disconnected, if the Battery Power and Caps Lock / Number Lock LEDs do not glow, there is either a very low change or no charge in the battery. Connect the AC power adapter, verify that the battery power LED glows, allow the battery to charge for 15 - 30 minutes and then attempt to start the computer. If it starts, run the battery test and calibrate the battery. If it does not start, if possible, connect a replacement battery to verify that the battery is the problem.
If the computer does not start after charging the battery, remove the battery and connect the AC power supply. Verify that the battery power LED glows, and then attempt to start the computer. If the LED still does not glow, either the AC adapter has failed, or there is a bad connection between the adapter and the system board. If possible, connect a different AC power adapter to verify that the adapter is the problem, or contact HP for support which may require a service event.
If the battery light LED (which looks like a lightning bolt  ) flashes, the battery has insufficient charge to start the computer. To resolve this error, try the following solutions.
) flashes, the battery has insufficient charge to start the computer. To resolve this error, try the following solutions.
 ) flashes, the battery has insufficient charge to start the computer. To resolve this error, try the following solutions.
) flashes, the battery has insufficient charge to start the computer. To resolve this error, try the following solutions.- Connect the notebook PC to AC power and attempt to start the computer again.
- Check the AC adapter to confirm that all of the plugs are securely seated.
- Determine if the power LED on the AC adapter is lit (if available) to verify that the computer is receiving AC power from the wall outlet.
- If the computer operates on AC power correctly, charge the battery for thirty minutes to one hour and then restart the computer.
 NOTE:Charging the battery for this length of time is called "trickle charging". Trickle charging is a continuous constant-current charge at a low rate, which recharges the battery slowly when it is in a deep discharge state. Deep discharge occurs when a battery is left unused for extended periods of time.
NOTE:Charging the battery for this length of time is called "trickle charging". Trickle charging is a continuous constant-current charge at a low rate, which recharges the battery slowly when it is in a deep discharge state. Deep discharge occurs when a battery is left unused for extended periods of time.
If a BIOS corruption error occurs (Blink code 2), you may not even notice the blink codes, because as soon as the computer recognizes the error, it restarts, attempts to recover the BIOS, and then restarts again. You may notice an extra-long startup process as a result, and a message indicating that the BIOS has been recovered may display on startup. If this occurs, update the BIOS on the computer. For more information, refer to the HP Notebook PCs - Locate and Install Updated BIOS, Drivers, and Software .
support document.
If you experience a memory failure (Blink code 3), follow the guide in the table below.
| If Using Original Memory | If New Memory Is Added |
|---|---|
| Reseat the memory. If reseating the memory does not resolve the problem, try replacing the memory with new memory. | Reseat the memory. If you continue to experience this error code after reseating the memory, the problem may be with the memory itself. Take the new memory out of the computer, put the original memory back into the computer, and then retest it. |
If you do not feel comfortable reseating the memory yourself, take the computer to a computer retailer and ask them to reseat it for you.

NOTE:Some memory module errors may allow the computer to start but will then cause the computer to restart and display a blinking error code.
A general system board failure (Blink code 5) is the failure of a component not covered by the other LED error codes. Contact HP for assistance.
The BIOS authentication error (Blink code 6) is extremely rare. It is the result of a discrepancy between the BIOS and the hardware that is installed on the computer. This error occurs when the BIOS cannot authenticate signatures from the hardware on the system. The purpose of the BIOS authentication is to be sure that no one has tampered with the BIOS on the computer.
If a BIOS authentication failure occurs, the computer automatically performs a BIOS recovery. If the computer does not automatically recover the BIOS, manually perform a BIOS recovery. To manually perform a BIOS recovery, press all four arrow keys at the same time to cause the BIOS to go to the EFI partition to find and recover the current BIOS.