Lync Server 2010 Deployment – Part 2
Where Part 1 left off was just shy of deploying the Standard Edition server itself as most of the back-end configuration was completed. A few additional steps will be left for later discussion (e.g. client Automatic Configuration DNS records) when those topics are addressed. So for now left’s get the Lync Server deployed an functional.
Update: This process is identical to (and has been tested with) the public release version of Lync Server 2010.
Install Lync Server System
What these steps do is install a second SQL Express named instance (this one being named
RTCLOCAL) on the local server which will contain a replica of the existing RTC named instance. Although it may initially seem inefficient to have two SQL instances with duplicate data on the same server the separation of the Central Management Store and a CMS replica is key to how multiple server’s function in a single organization.
Only the first Standard Edition server in the organization would contain this authoritative RTC instance, while all other Lync Front End Servers (and even Edge Servers) would contain their own RTCLOCAL instance to replicate the Central Management Store data. This approach also allows for the new redundancy and availability features which were lacking in previous versions of OCS. This RTCLOCAL instance can only ever be stored in an automatically installed SQL Express instance, it is not supported to locate this data in a full SQL Server instance.
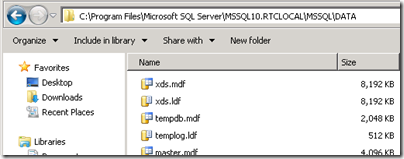
- Back at the Deployment Wizard main menu select Install or Update Lync Server System. Run Step 1: Install Local Configuration Store and leave the default setting to Retrieve the configuration data directly from the Central Management Store. By reviewing the results in the execution window we can confirm a number of actions, most importantly that the second SQL Express instance of RTCLOCAL was installed.
<snipped>
Checking prerequisite PowerShell2…prerequisite satisfied.
Checking prerequisite SqlExpressRtcLocal…installing…success
Checking prerequisite VCredist…prerequisite satisfied.
Checking prerequisite SqlNativeClient…prerequisite satisfied.
Checking prerequisite SqlBackcompat…prerequisite satisfied.
Checking prerequisite UcmaRedist…prerequisite satisfied.
Installing OcsCore.msi(Feature_LocalMgmtStore)…success
- Secondly the Local Configuration Store was installed and enabled using the Import-CsConfiguration and Enable-CSReplica cmdlets.
> Install Local Configuration Store Import-CSConfiguration -FileName "C:\Users\ADMINI~1.CSM\AppData\Local\Temp2\CSConfigData-2010_09_15-12_19_04.zip" -Verbose -LocalStore
> Enable local replica service Enable-CSReplica -Verbose -Confirm:$false -Report "C:\Users\administrator.CSMVP\AppData\Local\Temp2\Enable-CSReplica-[2010_09_15][12_10_23].html"
- To confirm the location of the RTCLOCAL database files on the server check the default SQL Server installation directory for the existence of the xds files.
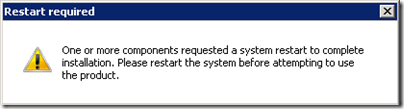
- Run Step 2: Setup or Remove Lync Server Components and if the process halts with an error requesting a reboot as shown below then restart the server and run this step again. This can occur because the Windows Media Format Runtime package requires a server restart after installation.
Checking prerequisite Wmf2008R2…installing…failure code 3010
The server must be restarted before installation can continue. To continue the installation after the server has restarted, start the Deployment Wizard and complete this step again.
- At the completion of this step all of the Lync Server services and components have been installed locally. A look at the Services applet will show a large list of installed services which are not yet running as a certificate still needs to be configured and assigned to them.
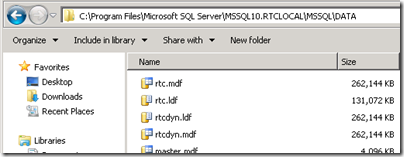
- Some of the newly added database files for the pool can be seen in the default SQL Server DATA directory as well.
So about now would be a good time to briefly sidebar and try to understand what is going on with all these different SQL instances and databases with similar names. I was scratching my head as well the first time I installed all this in an early beta release. So basically here is a brief rundown of
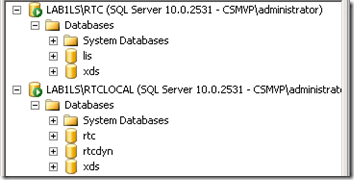
- Using SSMS there are two instances (both SQL Express) on the Lync Server, RTC and RTCLOCAL on the server to connect to, each with a different set of databases.
| Instance | Database | Description |
| RTC | lis | Location Information Services data |
| RTC | xds | Central Management Store data |
| RTCLOCAL | rtc | Standard Edition Pool data |
| RTCLOCAL | rtcdyn | Standard Edition transient user data |
| RTCLOCAL | xds | Local replica of Central Management Store data |
And now moving back into the server deployment the next pending step is to request and assign a certificate so that the services can be started.
- Run Step 3: Request, Install or Assign Certificates and then expand the Default Certificate entry to verify that all roles are checked. Click Request and enter the information listed in the following tables.
Delayed or Immediate Requests
| Send the request immediately to an online certificate authority |
Choose a certificate Authority
Select from a list detected in your environment
(LAB1DC.csmvp.net\CSMVP-RootCA) |
Certificate Authority Account
Specify Alternate Certificate Template
Name and Security Settings
| Friendly Name | Lync SE Certificate |
| Bit Length | 2048 |
Organization Information
| Organization | <Company Name> |
| Organizational Unit | <Department Name> |
Geographical Information
| Country/Region | United States |
| State/Province | IL |
| City/Locality | Chicago |
Subject Name / Subject Alternate Names
| Subject Name | lab1ls.csmvp.net |
| Subject Alternate Name | lab1ls.csmvp.net
dial.csmvp.net
meet.csmvp.net
admin.csmvp.net
external.csmvp.net |
SIP Domain setting on Subject Alternate Names (SANs)
| Configured SIP Domains | csmvp.net |
Configure Additional Subject Alternate Names
- This process will execute the Request-CsCertificate cmdlet with the provided configuration information, performing and online request against the CA and then automatically importing the return certificate into the Local Computer store.
> Request Certificate
Request-CSCertificate -New -Type Default,WebServicesInternal,WebServicesExternal -CA "LAB1DC.csmvp.net\CSMVP-RootCA" -Country US -State "IL" -City "Chicago" -FriendlyName "Lync SE Certificate" -KeySize 2048 -PrivateKeyExportable $False -Organization "Schertz Lab" -DomainName "sip.csmvp.net" -Verbose -Report "C:\Users\administrator.CSMVP\AppData\Local\Temp2\Request-CSCertificate-[2010_09_15][14_55_56].html"
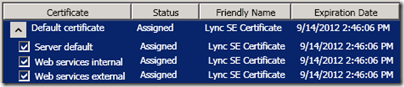
- Click Assign and select the new certificate from the local store. The following Set-CsCertificate cmdlet is automatically run by the wizard to assign the desired certificate to the three server roles.
> Assign Certificate
Set-CSCertificate -Type Default,WebServicesInternal,WebServicesExternal -Thumbprint 7B8E17E800F4702EC14228C4A6E84C019F9F6AB6 -Verbose -Confirm:$false -Report "C:\Users\administrator.CSMVP\AppData\Local\Temp2\Set-CSCertificate-[2010_09_15][15_03_04].html"
- Once the certificate is assigned to all roles the wizard should reflect that, although a Refresh may need to be required to see the changes.
- Run Step 4: Start Services to see the fruits of your labor converted into a bunch of happily-running services. The Start-CsWindowsService cmdlet is executed with no parameters which by default will attempt to start all Lync services.
> Start Services
Start-CSWindowsService -NoWait -Verbose -Report "C:\Users\administrator.CSMVP\AppData\Local\Temp2\Start-CSWindowsService-[2010_09_15][15_40_36].html"
Let us briefly take a look at another major difference between OCS and Lync which is how IIS is configured by the installation process.
- For one, certificates previously had to be manually defined and SSL enabled in IIS, but in Lync Server the setup wizard now does this automatically.
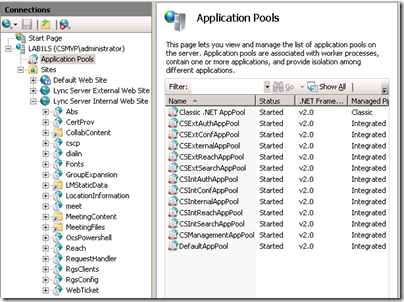
- The other noticeable difference is the amount of new Application Pool defined, as well as the separate internal and external web sites.
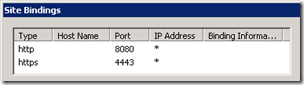
Because there was no step in the deployment asking for additional IP addresses and it is still a best practice to use a single IP address on the Standard Edition server the External and Internal web sites in IIS are clearly not configured on the same listening ports.
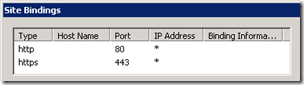
- The Lync Server Internal Web Site shows the default TCP80 and TCP443 ports assigned to it.
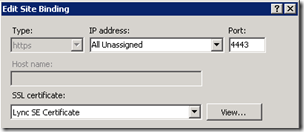
- Yet the Lync Server External Web Site indicates different listening ports of TCP8080 and TCP4443 ports. This configuration indicates that an external publishing server (e.g. ISA Server) must be configured to listen for client connections on the standard 80 and 443 ports yet it will forward traffic to the internal Front End server over ports 8080 and 4443 so that external client connections are directed to the External Web Site.
Before enabling user accounts now would be a good time to add the required internal DNS records to support Automatic Configuration. This is allow for any AD Integrated replication to fully propagate the new DNS records before attempting to sign-in with the Lync client.
- Create a DNS Service Locator (SRV) and Host (A) records on the internal DNS server’s forward lookup zone.
As a general best practice I always prefer to add a second DNS record which the client will use as a fallback during Automatic Configuration in the case that the SRV record is not available or unsupported. The Communicator and Lync clients will automatically lookup
sipinternal,
sip, and
sipexternal host records in the SIP domain if the SRV lookup first fails.
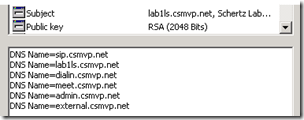
- A quick look at the details of the requested certificate shows an additional entry for sip.csmvp.net in the Subject Alternate Name field even though it was now specifically entered in the certificate wizard. The ‘Configured SIP Domain’ which was identified as csmvp.net during the setup automatically added a “sip.” record for that domain, so that record will suit our purposes.
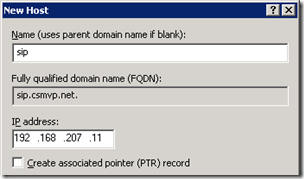
- Create a new DNS Host (A) record on the internal DNS server’s forward lookup zone for the desired SIP domain (e.g. sip.csmvp.net) and provide the same IP address which is statically assigned to the Lync Front End server.
- Verify the new records using the following nslookup commands from the standard Windows Command Prompt.
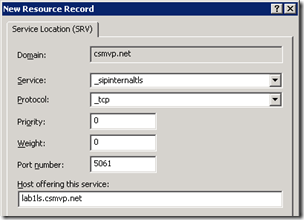
C:>nslookup -q=srv _sipinternaltls._tcp.csmvp.net
_sipinternaltls._tcp.csmvp.net SRV service location:
priority = 0
weight = 0
port = 5061
svr hostname = lab1ls.csmvp.net
lab1ls.csmvp.net internet address = 192.168.207.11
C:>nslookup sip.csmvp.net
Name: sip.csmvp.net
Address: 192.168.207.11
Lync Control Panel
In a major shift away from MMC-based management consoles Lync Server can only be managed by either the Silverlight-based
Lync Server Control Panel or the PowerShell-based
Lync Server Management Shell.
- Launch the Lync Server Control Panel from the Microsoft Lync Server 2010 (RC) program group and re-enter the current account’s credentials. (Make sure this account has been added to the CsAdministrator domain group as covered in the Part 1 article.)
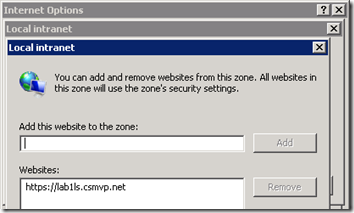
- (Optional Step) In order to suppress the additional authentication prompt when opening the control panel then on local server go to Internet Options > Security > Local Intranet > Sites > Advanced and add the FQDN of the Lync Server to the zone (e.g. https://lab1ls.csmvp.net).
At this point we should have a fully functional Lync Server and are ready to start configuring accounts, policies, and additional services. Part 3 in this series moves on to enable a few user accounts for Lync Server to test client connections to the Front End server.



No comments:
Post a Comment