Lync Server 2010 Deployment – Part 1
Now that the general public has access to the Release Candidate software for Lync Server 2010 it is now appropriate to cover the deployment process in depth. The purpose of this article is to take a look at what the installation process actually does in order to generate a deeper understanding of the product. Not just simply follow a bunch of screenshots of the deployment wizard.
I’m starting with the Standard Edition as this is both the simpler approach and the more common deployment for testing purposes. A host of new features and concepts have been introduced which are all available in single-server Standard Edition pool, not to mention that the required amount of individual physical hosts have been reduced thanks to improved collocation support. So a single Windows Server can now fill the role of both a consolidated Standard Edition server and a Mediation server. Additional roles like the Monitoring Server can also be collocated with the Standard Edition server, but a full SQL Server installation must be performed on the server prior to deploying Lync Server on it. Previous versions of OCS Standard Edition did not support this level of co-mingling, or support anything but the default SQL Express instance.
For the purposes of this walkthrough I will start to introduce a number of PowerShell cmdlets in some of the processes, but understanding that PowerShell may still be new to many people I will utilize the deployment wizard throughout the majority of the steps. Later on I plan to document a complete Lync Server deployment using PowerShell cmdlets at every possible step.
Much of this process is already detailed in Microsoft’s official
Lync Server 2010 (RC) Lab Deployment Guide but I’ve gone into further details on many of the steps, as well as mixed up some of the order as a few of the prerequisite steps are redundant. That document also includes configuration and deployment steps for a Director and Edge Server which I will not cover now, but will address in later articles.
Update: This process is identical to (and has been tested with) the public release version of Lync Server 2010.
Environment
- Physical Host: Windows Server 2008 R2 Hyper-V running on a Core2 Duo desktop-class system with 8GB RAM.
- Domain Controller: A single Windows Server 2003 guest promoted to a domain controller for the new Active Directory forest root domain of csmvp.net. (Newer versions of Windows Server 2008 can be used but for the sake of saving precious RAM resources on my lab server I opted for Server 2003.)
- Lync Server: A second virtual guest running Windows Server 2008 R2 x64 Enterprise and joined to the csmvp.net domain.
- The domain account used to perform all steps is a member of the Domain Admins, Enterprise Admins, and Schema Admins domain security groups.
- The Forest and Domain functional levels were elevated to Windows Server 2003.
- A Windows Enterprise Certificate Authority was deployed on the DC.
Active Directory Preparation
Before we can run any of the AD preparation steps included in the deployment wizard a few server prerequisites must first be installed. The various IIS features are not required until just prior to deploying the Lync Server components but for simplicities sake installing all features in one step is best.
- Launch Windows PowerShell buy selecting ‘Run As Administrator’ and enter the following cmdlets to quickly install the .NET Framework 3.5.1 package, the Remote Server Administrative Tools, and all IIS7 features then perform the required server reboot. (The Telnet Client is not a requirement but I always install the feature as it is a handy troubleshooting tool. If Windows Server 2008 SP2 is used then PowerShell 2.0 will also need to be installed).
PS C:> Import-Module ServerManager
PS C:> Add-WindowsFeature NET-Framework,RSAT-ADDS,Telnet-Client,Web-Server,Web-Static-Content,Web-Default-Doc,Web-Http-Errors,Web-Http-Redirect,Web-Asp-Net,Web-Net-Ext,Web-ISAPI-Ext,Web-ISAPI-Filter,Web-Http-Logging,Web-Log-Libraries,Web-Http-Tracing,Web-Windows-Auth,Web-Client-Auth,Web-Filtering,Web-Stat-Compression,Web-Mgmt-Console,Web-Scripting-Tools -Restart
- From the installation media launch the setup wizard found at the following location:
\Setup\amd64\setup.exe
- At this point the setup will automatically ask to install the Microsoft Visual C++ 2008 Redistributable x64 package. Confirm and wait for the next setup window to appear. (It may take a minute as the installation runs in silent mode, but also keep an eye on the taskbar as the installation window likes to pop-up behind other windows. Also note that this process no longer leaves a bunch of files on the root of the drive where it is installed as the previous OCS installation used to.)
- Accept the default Installation Location, or enter a different path, and select Install. Then accept the End User License Agreement.
C:\Program Files\Microsoft Lync Server 2010
- From the main menu select Install Topology Builder to install the Administrator Tools on the local server. This will install the Lync Server Management Shell which will be used to execute a few cmdlets to verify various AD preparation steps.
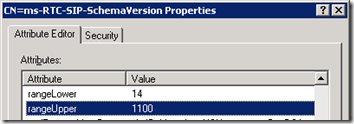
- From the Deployment Wizard select Prepare Active Directory. Run Step 1: Prepare Schema and review the log to verify no errors were reported. Verify the process using has completed successfully by checking the rangeUpper (1100) and rangeLower (14) values of the ms-RTC-SIP-SchemaVersion Schema object with adsiedit.msc.
- Run Step 2: Prepare Forest and use the settings in the table below. Review the results log to verify no errors were reported.
| Universal Group Location | Local Domain |
- Verify that the forest preparation was successful by executing the following cmdlet from the Lync Server Management Shell and looking for a response of LC_FORESTSETTINGS_STATE_READY.
PS C:> Get-CsAdForest
LC_FORESTSETTINGS_STATE_READY
- Run Step 3: Prepare Domain and review the log to verify no errors were reported. Verify that the process was successful by executing the following cmdlet from the Lync Server Management Shell and looking for a response of LC_DOMAINSETTINGS_STATE_READY.
PS C:> Get-CsAdDomain
LC_DOMAINSETTINGS_STATE_READY
Server Preparation
In previous beta builds a number of prerequisite supporting installations had to be manually deployed, but in the Release Candidate we see our first glimpse of how the upcoming RTM product will smoothly handle all of these for us.
This process will install the
SQL 2008 Native Client and
SQL Server 2008 Express, as well as configure firewall exceptions for SQL. Mostly importantly it also deploys the first SQL Express named instance, simply called RTC. This instance will be the default location for the Central Management Store which is where Lync will store the majority of the global (forest-wide) configuration data. The RTC Service container in the AD Configuration partition is still used to store some data, but mainly for coexistence with previous versions of OCS.
- From the main Deployment Wizard menu select Prepare first Standard Edition server.
<snipped>
Checking prerequisite WMIEnabled…prerequisite satisfied.
Checking prerequisite NoOtherVersionInstalled…prerequisite satisfied.
Checking prerequisite SupportedOS…prerequisite satisfied.
Checking prerequisite PowerShell2…prerequisite satisfied.
Checking prerequisite VCredist…prerequisite satisfied.
Checking prerequisite SqlNativeClient…installing…success
Checking prerequisite SqlBackcompat…prerequisite satisfied.
Checking prerequisite UcmaRedist…prerequisite satisfied.
Checking prerequisite SqlExpressRtc…installing…success
> Creating firewall exception for SQL instance
netsh advfirewall firewall add rule name="OCS SQL RTC Access" dir=in action=allow program="c:Program Files\Microsoft SQL Server\MSSQL10.RTC\MSSQL\Binn\sqlservr.exe" enable=yes profile=any
Ok.
> Creating firewall exception for SQL Browser
netsh advfirewall firewall add rule name="SQL Browser" dir=in action=allow protocol=UDP localport=1434
Ok.
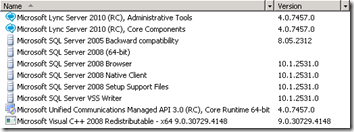
- A quick glance at the Programs and Features control panel shows all of the components which were just installed.
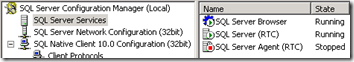
- Also locate and launch the SQL Server Configuration Manager to verify the local SQL services are properly installed and running.
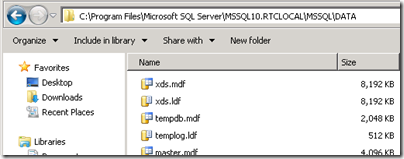
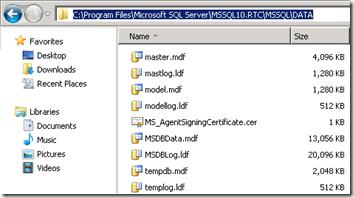
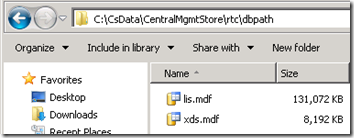
- The newly installed SQL Server Express instance default database files can be found in the following default location:
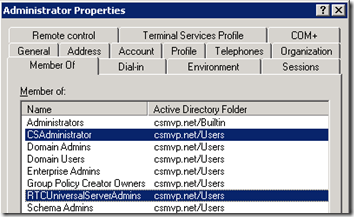
- In a slight change from previous versions of Communications Server it’s not enough to simply be logged in as a Domain Admin to fully administer the Lync Server environment. Before moving further the domain Administrator account used throughout this process should be added as a member to the domain security groups CsAdministrator and RTCUniversalServerAdmins.
- This user account should then logoff and back on to the Windows Server where Lync is being installed to update the associated security token. Once logged back on use the following commands in the Windows Command Prompt to verify the new group membership:
C:> whoami /groups /fo list | findstr /i CsAdmin
Group Name: CSMVP\CSAdministrator
C:>whoami /groups /fo list | findstr /i RTCUniv
Group Name: CSMVP\RTCUniversalGlobalReadOnlyGroup
Group Name: CSMVP\RTCUniversalUserReadOnlyGroup
Group Name: CSMVP\RTCUniversalServerAdmins
Group Name: CSMVP\RTCUniversalServerReadOnlyGroup
Group Name: CSMVP\RTCUniversalGlobalWriteGroup
The final preparation step is to manually create a file share on the server which will later be referenced during the Lync Server topology configuration.
- Create a new folder on the server named lyncshare anywhere on the server. The following path was used in this lab deployment:
C:\Program Files\Microsoft Lync Server 2010\LyncShare
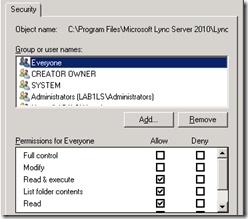
- Configure the NTFS file security on the new folder to grant Read & Execute permissions to Everyone.
- Also verify that the Administrators group is already granted Full Control.
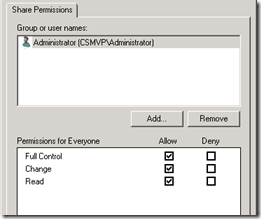
- Then enable file sharing with the Share name of lyncshare and configure the share permissions so the administrator account used to perform the installation is granted Full Control. A later server deployment process will customize the share and file permissions accordingly.
Topology Builder
Because the Lab Deployment Guide uses the Planning Tool and this is not required I will instead walkthrough the basic Topology Builder process.
- Launch the Lync Server Topology Builder application found in the Microsoft Lync Server 2010 (RC) program group.
- Select New Topology from initial prompt and save the .tbxml file with any desired name (e.g. chicago.tbxml).
- For the Primary SIP domain enter the desired domain namespace (e.g. csmvp.net). This does not have to be the same namespace utilized by Active Directory. If an Exchange Server or other messaging platform exists in this forest then whatever the current primary SMTP namespace is should typically be selected as the SIP domain as well.
- Do not add an additional supported domains at this point unless desired. A single SIP domain is sufficient to test all of the features of Lync Server in a lab environment.
- Define the Name (e.g. Chicago) and Description (e.g. Main Site) of the first site. This is also a new component of Lync Server as previous versions did not include and type of site definition. The site information will be used by many of the new resiliency features in Lync Server.
- Provide City, State/Province, and Country/Region Code information specific to your first site.
- Complete the topology definition and open the New Front End Wizard.
- In the Define New Front End Pool wizard select the following options and enter the desired information specific to your own lab. The pool FQDN should be the FQDN of the server where you will be installing the Lync Server Standard Edition server components.
Define the Front End Pool FQDN
| FQDN | lab1ls.csmvp.net |
| Type | Standard Edition Server |
Select Features
- Conferencing, which includes audio, video, and application sharing
- Dial-In Conferencing
- Enterprise Voice
- Call Admission Control
Select Collocated Server Roles
- Collocate A/V Conferencing Server
- Collocate Mediation Server
Associate Server Roles with this Front End Pool
- (Leave all options unchecked )
Define the SQL Store
- Because this is a standard Edition installation and SQL Express has already been deployed all options are disabled. The default RTC instance on the local server will be used.
Define the File Share
| File Server FQDN | lab1ls.csmvp.net |
| File Share | lyncshare |
Specify the Web Services URL
| Internal Base URL | lab1ls.csmvp.net |
| External Base URL | external.csmvp.net |
Specify PSTN Gateways
- Leave these options blank for now as Enterprise Voice will be enabled in a later article.
- Back at the main Topology Builder window select Edit Properties on the Lync Server 2010 (RC) root-level object. Highlight the Simple URLs section and enter the desired Administrative Access URL. (Note the additional for Phone Access URLs and Meeting URLs are already configured.)
https://admin.csmvp.net
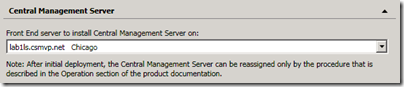
- Also highlight the Central Management Server section and select the new Front-End server from the drop-down menu if it is not already selected.
At this point it is now time to publish the topology which will populate the RTC instance with new databases, create the folder structure in the shared directory, and publish configuration settings into the CMS and Active Directory.
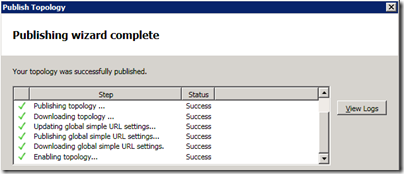
- From the Action menu select Publish Topology. Select the local server FQDN for the Central Management Store location which should be the only option in the drop-down menu. If all previous configuration steps were completed correctly then the wizard should complete successfully.
As indicated by the
To-Do List shown under
Next Steps a couple of DNS records will need to be manually created to match the FQDN set in the Lync Server topology.
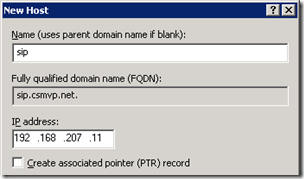
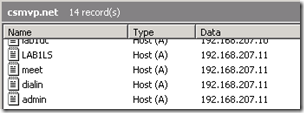
- Create new DNS Host (A) records on the internal DNS server’s forward lookup zone which matches the SIP domain used. Each record should point to the static IP address used by the server where the Standard Edition roles will be deployed.
To validate and understand the changes the Topology Builder has applied to Active Directory there are a number of places to look throughout the various results logs, within Active Directory, and the SQL databases themselves.
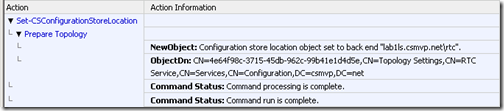
- Highlight Setting Central Management Store location… on the Publishing wizard complete window and select View Logs. This log shows that the Set-CsConfigurationStoreLocation cmdlet was used to define the location of the CMS for all future Lync Servers to know how to locate the forest’s configuration data.
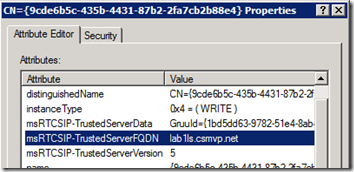
- Use adsiedit.msc to view the Configuration context and browse to the path shown below. View the properties on the only object in the Global Settings container to see that the supplied configuration data among the attribute values. Also note that the whenCreated attribute should coincide with the time the topology was just published.
CN=Global Settings,CN=RTC Service,CN=Services,CN=Configuration,DC=csmvp,DC=net
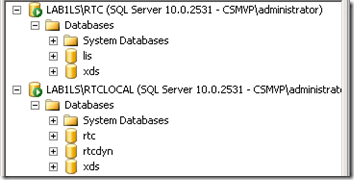
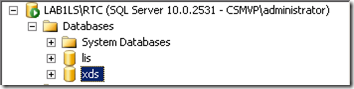
- From another computer on the network with SQL Server 2008 Management Studio Express installed the SQL Server Management Studio can be used to connect to the RTC instance on the Lync Server to view the databases. Here we see the XDS and LIS databases created by the CMS setup.
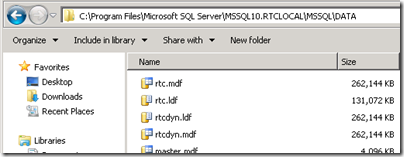
- The raw database files can be found on the Lync Server in the default installation directory shown below.
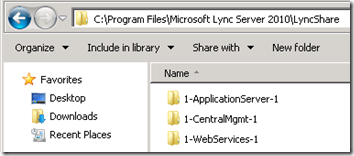
- Additionally the manually defined file share is now populated with new folder structure.
Summary
At this point all organization preparation steps have been completed and the next step is to actually install the Standard Edition server components
.
The next article in this series jumps right into that process with Part 2.
http://blog.schertz.name